Due Dates
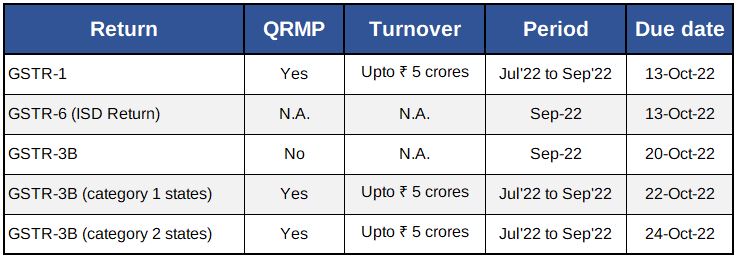
GST Due Dates
Corporate Laws Due Dates
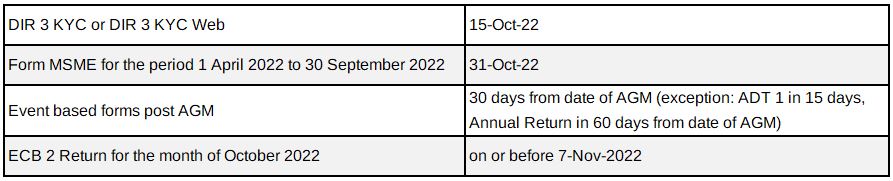
Due Dates
Company Law - Notification / Circulars
- MCA vide notification dated 15 September 2022 has increased the threshold limits to determine if a Company is a small company or not. Revised threshold is paid up capital not exceeding ₹4 Crores and Turnover not exceeding ₹40 Crores. Consequent to this increase in threshold limits, more Companies will fall under the definition of Small Company. Small Companies have lesser compliances compared to other companies.
- MCA vide notification dated 20 September 2022 amended the Companies (Corporate Social Responsibility Policy) Rules, 2014. As per the amendment rules, below are the changes:
- Companies falling under Section 135(1) are required to constitute CSR Committee as per threshold limit during the immediately preceding financial year. The amendment has been made in similar lines in the rules by omission of the requirement to continue with compliance of Sec.135 upto three financial years for companies that would cease to be covered under the section.
- Companies having unspent amounts relating to ongoing project in designated accounts that are required to utilize the same within three financial years will have to constitute CSR Committee if not applicable under Section 135 to oversee the utilization OR the CSR Committee already constituted will have to be continued and cannot be dissolved
- A new class of entity i.e. entities exempted under sub-clauses (iv), (v), (vi) or (via) of clause (23C) of section 10 of the Income Tax Act, 1961, that may act as an implementing agency has been introduced which broadly covers institutions for public religious and charitable purposes, university, hospital or other educational institutions established for the purpose prescribed in the said section.
- The eligible expenditure for impact assessment was lower of 5% of the total CSR expenditure for that financial year or fifty lakh rupees, which has now been amended to higher of 2% of the total CSR expenditure for that financial year or fifty lakh rupees. Hence, this has increased the limits of booking expenditure in case of large CSR projects
- A new format has been substituted for the annual report on CSR activities to be included in the board’s report for the financial year commencing on or after April, 2020.
- Reserve Bank of India vide A.P. (DIR Series) Circular No. 16 has brought uniformity in imposition of Late Submission Fee (LSF) across functions. Please refer attached circular for calculation of LSF.
Customs and Foreign Trade Policy update
Government extends validity of Foreign Trade Policy by further six months - Notification 37/2015-2020, dated 20th September 2022
In July 2022, the Reserve Bank of India (RBI) issued A.P. (DIR Series) Circular No.10 permitting international trade settlement in Indian Rupees. In sync with this RBI Circular, the Government has amended the Foreign Trade Policy to permit invoicing, payment and settlement of exports and imports in INR. Under this mechanism, the payment for imports would be made by the importers in INR and the same would be credited into the Special Vostro account of the correspondent bank of the partner country maintained with AD Bank in India. In case of exports from India, Indian exporters would be paid the export proceeds in INR from the balances in the said Special Vostro account.
Government amends FTP to permit invoicing, payment and settlement of exports and imports in INR
Foreign Trade Policy 2015-2020 was originally valid for five years up to 31 March 2020, which was subsequently extended up to 31 March 2022, and then extended till 30 September 2022. Now, the Government has further extended the validity of Foreign Trade Policy 2015-2020 and the Handbook of Procedures by another six months till 31 March 2023. FTP inter alia provides various export promotion/incentive schemes such as EPCG, Advance Authorization, EOU, STP etc. Such schemes now would continue to operate in their present form up to 31 March 2023.
EPCG scheme - extension of time limit to submit report of fulfilment of export obligation for the
2022-23 - Public notice No. 27/2022
The time limit to file report of fulfilment of export obligation under para 5.15 of the Handbook of Procedures is extended from September 30, 2022 to 31 December 2022 for the year 2022-23.
DIRECT TAX
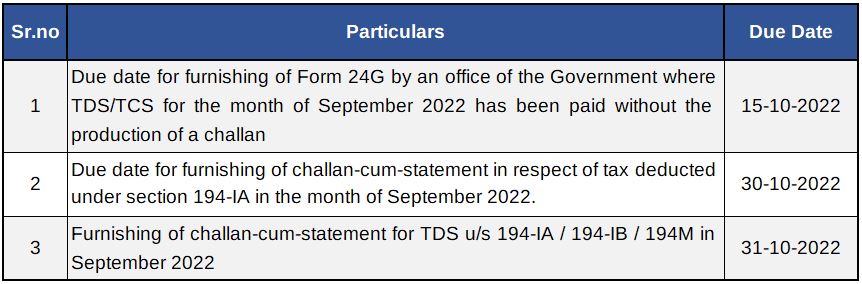
Important Due Dates October 2022
Circulars / Notifications / Press Release
Notification No. 105/2022
- CBDT amends Rule 114BB by inserting a proviso to exclude Central Government, State Governments and Consular Offices from the requirement of quoting PAN or Aadhaar Number for cash deposit(s) in or withdrawal(s) from a bank or a post office aggregating to ₹ 20 Lac or more in a financial year and will come into effect from 9 Jul 2022.
Notification No. 109/2022
- The Government has widened the scope of section 285B to include persons engaged in ‘specified activities’ to expand reporting requirements in Form 52A and to include persons engaged in event management, documentary production, etc. Form 52A must be filed electronically within 60 days from the end of the previous year.
Notification No. 110/2022
- Rule 12AD has been inserted and comes into effect from 1 November 2022. The modified return of income to be furnished by a successor entity to a business reorganization, as referred to in section 170A, for an assessment year, will be in the Form ITR-A and verified in the manner specified therein.
Notification No. 111/2022
- CBDT has notified Form 69 for re-computation of total income after disallowing cess or surcharge claimed and allowed as deduction under Section 40(a)(ii) since AY 2005-06. For this Assessee is required to file application in Form 69 to be made on or before 31 Mar 2023 detailing the additional taxes payable. After this Assessee is then required to make the payment of tax and intimate about it to the Assessing Officer in Form 70 within 30 days of making the payment.
Circular No : 18/2022
- One-time loan settlement with borrowers or waiver of loan granted on reaching settlement with the borrowers by the banking or financial institutions will not be subjected to TDS u/s194R.
- Amount incurred by “pure agent” (as defined in GST Act) for which he is reimbursed by the recipient of service would not be treated as benefit/perquisite for the purpose of section 194R and hence no tax is to be deducted.
- If out-of-pocket expenses (reimbursement) are already part of the consideration in the bill and tax is deducted on amount including out-of-pocket expense under any other TDS section, other than section 194R, then there will not be further liability for TDS u/s 194R.
- If benefit/perquisite is provided in a group activity in a manner that it is difficult to match such benefit/perquisite to each participant using a reasonable allocation key, the benefit/perquisite provider may at his option not claim the expense, while calculating his total income. If he decides to opt so, he will not be required to deduct TDS u/s 194R.
- TDS u/s 194R is not required to be deducted on issuance of bonus or right shares by a company in which the public are substantially interested as defined in clause (18) of section 2 of the Income-tax Act, where bonus shares are issued to all shareholders by such a company or right shares are offered to all shareholders by such company.
Case Laws
M/s. Koninklijke Philips N.V Vs Deputy Commissioner of Income Tax
- Assessee is a non-resident company incorporated in Netherland and received an Interest on Income Tax refund after deduction of TDS for which Assessee appealed before ITAT.
- ITAT observes that interest mean a “debt claim” of any kind and also observes that as per India-Italy DTAA, any “debt claim” payable by government is exempt and as a result such Interest is a debt-claim on which no TDS is liable to be deducted.
Vinodkumar Lakshmipathi Vs Commissioner of Income Tax
- Assessee an individual claimed Foreign Tax Credit in return which was denied by revenue on ground that he had filed the Form 67 along with return of income after the expiry of extended due date of filing the income tax return which is contravention as per Rule 128(9).
- Aggrieved by this assessee filed appeal before CIT(A) who upheld the Assessing Officer’ view. This was further appealed by the Assessee before ITAT and ITAT ruled in favour of Assessee by clarifying that Form No. 67 is directory requirement and does not provide for disallowance of Foreign Tax Credit.
M/s. Brocade Communications Systems Pvt. Ltd. Vs The Principal Commissioner of Income Tax
- In respect of Brocade Communications Systems Pvt. Ltd, PCIT had initiated revisionary proceedings and revised the final order which was passed in line with the directions of the DRP.
- Assessee relied on Mumbai ITAT’s ruling in Barclays Bank PLC but Revenue relied on ruling of Adamas Builders Pvt Ltd that rejected the reasoning held in Barclays Bank PLC on the premise that if there was an error in the draft assessment order on failure to make enquiry on an issue which ought to have been examined, then the only remedy for the revenue was to invoke jurisdiction.
- Matter reaches ITAT and ITAT held that if any issue had not been considered and decided by the First Appellate Authority, then on such matters, the CIT has powers to exercise revisionary jurisdiction if AO failed to make necessary enquiries before concluding the assessment.
- Assessee received free goods from its associated enterprise and Pr. CIT was of the view that the asset received free of cost is deemed as income and with this view ITAT upheld the matter in favour of Pr. CIT and Assessee’s income was adjusted accordingly.
MAHASHIAN DI HATTI PVT. LTD Vs DCIT
- Revenue issued notice stating that assessee had escaped assessment on account of 28 bogus entries received from an entry provider and received notice for which senior counsel of assessee stated that revenue failed to comply with the direction of Supreme Court in the case of Union of India vs. Ashish Agarwal.
- Hearing the facts in the case, HC sets aside the notice issued stating it is vague and violative of principal of natural justice.
Nilesh M. Agrawal Vs Deputy Commissioner of Income Tax
- In the referred case, assessee was subject to a search operation consequent to the search operation of the group companies where he was a promoter and admitted to have provided accommodation entries to various beneficiaries through paper concerns.
- Revenue during the course of assessment made additions for the relevant AYs on account of unexplained purchases at 30%, addition on claim of receivables, loans received , etc.
- Matter reaches to ITAT which ruled that statements recorded during search cannot be used on a standalone basis to make additions in the post-search assessments and deletes additions made in the post-search assessments
Nitin Prakash Vs DCIT:
- Assessee sold residential flats which was purchased on instalments in AY 2005-06 and calculated indexed cost of acquisition taking the CII of AY 2005-06.
- Revenue rejected Assessee’ s computation of indexed cost of acquisition and recomputed the same at ₹ 2.55 Cr by allowing indexation and making an addition of ₹ 45.94 Lacs on account of long-term capital gains.
- Matter reaches to ITAT which ruled that the asset was held by the Assessee on the date of issuance of allotment letter, when initial amount was paid and the flats were booked, thus he was entitled to claim the benefit of indexation.
ANI Technologies Private Limited Vs DCIT:
- Assessee is a transport aggregator platform and Revenue held ANI technologies to be assessee in default because assessee had not deducted tax on payments made to drivers.
- Matter reaches to ITAT which ruled that no liability u/s 194C for providing transport aggregator platform, in respect of payments made to the drivers.
Goods and Service Tax
Pre-deposit for filling an appeal can be made by utilizing balance in Electronic Credit Ledger- Bombay High Court
The Bombay High Court in a writ petition filed M/s Oasis Reality has held that the requirement of pre-deposit of disputed demand for filing an appeal under the GST law can be complied with by utilizing the balance available in electronic credit ledger. The Hight court referred to a clarification issued by CBIC in Circular F. No. CBIC-20001/2/2022-GST dated 6th July 2022 that balance in electronic credit ledger can be utilized for any amount payable towards output tax whether self-assessed in return or payable as per the consequence of any proceedings under law. Since, the amount payable by the petitioner was towards output tax, the court held that the petitioner could utilize the amount available in electronic credit ledger.
No input tax credit on procurement of vouchers and subscription packages which are made available to customers free of cost against redemption of loyalty points – Karnataka AAR
The Karnataka AAR in the case of M/s Myntra Designs Private Limited has held that, the applicant is not eligible to avail input tax credit on the vouchers and subscription packages procured by them from the third-party vendors, that are made available to eligible customers in the loyalty program.
The applicant in this case contended before the AAR that the expenditure incurred is “in the course or furtherance of business” and accounted as expenditure in books related to business and further stated that the third-party vendors raised their invoices in respect of sale of vouchers and subscription packages by classifying their outward supply under the SAC 9983 as “other professional, technical and business services” being termed as ‘supply of services’. Further, considering that the restriction under section 17(5)(h) of the Central GST Act is applicable only in respect of goods disposed of by way of gifts; the said restriction on input tax credit would not be applicable in their case because what is given as gift to the customers is a ‘service’ and not ‘goods’.
The AAR however rejected the contention of the applicant and in support of its ruling noted that:
- Subscription packages are a “voucher” as per section 2(118) as it places obligation on the potential supplier to accept it as a consideration of supply of goods or services to the holder of the instrument, that is, the customer.
- The vouchers are a movable property which are available in tangible form and are capable of being transmitted electronically; thus, they qualify as ‘goods’ as per section 2(52) of the Central GST Act.
- The supply of vouchers in the instant case involves transfer and hence it ought to be classified as ‘supply of goods’ as per schedule II of section 7 of the Central GST Act.
- The redemption of loyalty points by the customers for receiving voucher from the applicant implies that the voucher is issued free of cost to the customers and amounts to disposal of voucher by way of gift.
Having regard to the above, the AAR ruled that the applicant is not eligible for input tax credit on procurement of vouchers and subscription packages. It is interesting to note in this case that the AAR chose to ignore the classification of supply as adopted by the supplier and independently arrived at classification of supply to decide eligibility to input tax credit.
Cybersecurity / IS AUDIT
Zero Trust Policy: An Emerging & Warranted Philosophy
Cybersecurity, vast and extensive as it is, is generally considered a purely technical domain. Having said that, the approach of each company to its security would have a philosophical bent. As a technical domain, the field of computer science has never shied away from using philosophies to describe its dilemmas, like the Philosopher’s Chopstick to describe a deadlock and many others. That is because Computer Science and philosophy share a foundation rooted in logical reasoning. Computer scientists and programmers use mathematical and symbolic form of logic to build hardware and software products. Philosophy uses words to logically examine ideas and concepts. This writeup is quite simple to comprehend though. We will analyse the idea of Zero trust policy and see how important it is in today’s world of cybersecurity – especially when majority of our teams move rapidly in to cloud / hybrid infrastructure.
Zero Trust Security is a foundational element, a philosophical approach to security that is essential for every organization, business, or entity with an online presence. In layman’s term, this policy works on the assumption that you simply cannot separate the “good guys” from the “bad guys”. The traditional methods of establishing a strong perimeter to keep out the malicious actors have been long out of date. Our assets or resources that is the data, applications, infrastructure, and devices are increasingly hybrid or outside of the perimeter that we have strongly set up.
With Zero Trust, no actor can be trusted till they are verified. As far all the other strategies are concerned, this one has a holistic approach to security which ensures that everyone and all the devices granted access are who and what they claim to be. In the current digital age, data is spread across innumerable services, applications, devices, and people. Setting up a password protection or firewall or some other kind of perimeter is not enough in today’s world. In this age of digital transformation, perimeters don’t exist, and the old parameters of security doesn’t stack up to the sophistication of today’s threats.
The elements of the Zero trust security are straight forward and uncomplicated. We could boil it down to the three core principles:
- Verify every user
- Validate every device, and
- Intelligently limit access.
Being simple doesn’t mean it is easy to execute. However, for organizations choosing the Zero Trust Policy, it simply becomes how security happens.
Verify Every User
Today, organizations rely on only one verification method such as Single sign-on (SSO) which has a lot of advantages. Users don’t have to type passwords every time to use or access something and could reduce the number passwords they have to manage.
But, let us look at a few hypothetical situations. What if THAT one password is compromised orwhat if someone forgets to lock their system? In those cases, SSO lead to a security gap.
To avoid such issues, SSO needs to be balanced with Multi-Factor Authentication (MFA). Ultimately, you need to balance security and end user experience. But, it may be too onerous for end users to be constantly asked for additional factors of authentication.
Validate Every Device
Nowadays, nearly everyone has their devices locked down with a password of some sort, and that is unequivocally a great thing. Remember, however, that passwords are only one piece of the puzzle. To ensure real safety, devices must also have adaptive MFA to go along with that password.
When MFA-supported passwords are combined with some level of device management, the right policies are put on the device and locked in place, and the context of the device (where it’s used, what browser it has, etc.) is always understood, then it’s safe to make an access decision.
Intelligently Limit Access
The next aspect to discuss in the Zero Trust Security is the resources of the organization and who uses it. Make sure that on day one, an user is productive, they have access to the accounts they need, and devices are set up with the clients they need. When they change roles, their access likewise changes to fit their new job / role, or if they leave, those privileges are automatically revoked.
Most importantly, it is essential that all these capabilities are integrated and work together so that they can be applied in real time without adding delays to access decisions for APIs, or for users who are logging onto applications.
The Zero Trust strategy is result oriented. Beyond protecting valuable data by reducing the chance of breach, studies have shown that this approach has resulted in 50% fewer breaches and companies have spent 40% less on technology as everything is integrated. Also, recently aForrester study pointed that companies that adopted the policy are more confident in their ability to implement new business model and customer experience to the market. Thus, we can say, Zero Trust Infrastructure, is one line everyone can get behind.
SINGAPORE UPDATES
Monetary Authority of Singapore and Other Updates
1) MAS information paper on Strengthening AML/CFT Practices for External Asset Managers
The Monetary Authority of Singapore published an information paper on” Strengthening AML/CFT Practices for External Asset Managers”. This information paper is based on thematic inspections and engagements on anti-money laundering and countering the financing of terrorism (AML/CFT) conducted by MAS of selected external asset managers (“EAMs”). It sets out MAS’ supervisory expectations for effective AML/CFT frameworks and controls and includes good practices and illustrative examples observed. Its learnings should also be considered by other financial institutions.
MAS highlighted the following conclusions from their information paper:
- Governance – in particular the role and responsibility of board and senior management in maintaining good governance and sound AML/CFT risk management frameworks and controls;
- Enterprise-wide Risk Assessments (“EWRA”) – in particular on conducting adequate and robust EWRAs, as well as monitoring and periodically reviewing/updating the EAM’s EWRA;
- Customer risk assessment – in particular on considering relevant risk factors to identify, assess and understand the money-laundering and terrorism financing risks posed by a customer, and to apply the appropriate level of customer due diligence (“CDD”) and ongoing monitoring measures;
- CDD measures conducted on customers – in particular on ensuring that CDD measures are conducted thoroughly and in a timely manner, conducting effective transaction monitoring based on a sound transaction monitoring framework, and conducting periodic reviews of business relations with the EAM’s customers with the appropriate follow up measures;
- Enhanced CDD – in particular on identifying customers with a higher ML/TF risk, and conducting appropriate enhanced CDD measures and monitoring; and
- Suspicious transaction reporting – in particular on identifying suspicious transactions, ensuring that suspicious transaction reports are filed in a timely manner, and conducting appropriate risk mitigation measures.
2) MAS releases circular on enhancing AML/CFT in the VCC sector
The Monetary Authority of Singapore (“MAS”) has released a circular setting out key observations and expectations for effective anti-money laundering (“AML”) and countering the financing of terrorism (“CTF”) frameworks and controls following an industry-wide survey of Variable Capital Companies (“VCCs”) and a series of thematic engagements of eligible financial institutions (“EFIs”) to assess the effectiveness of their AML/CFT risk management and controls.
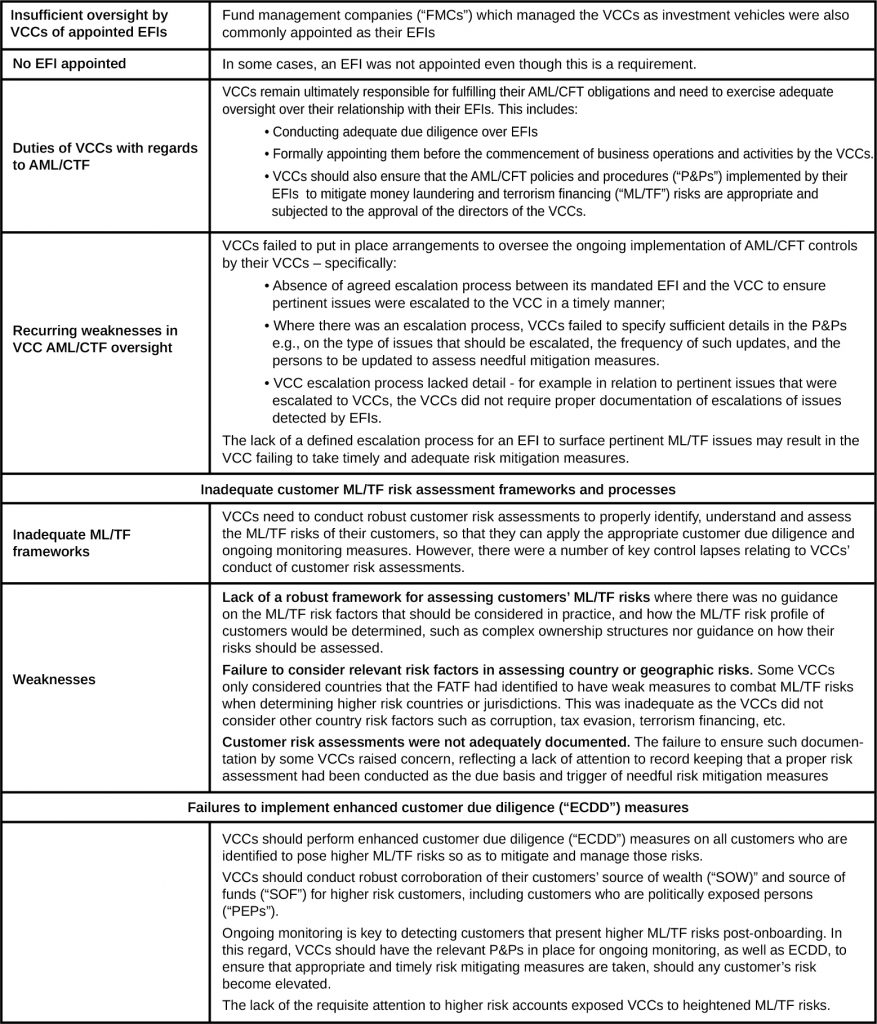
Key Observations
Insufficient oversight by VCCs of appointed EFIs
3) Business Trusts (Amendment) Bill Introduced to Align with Regulatory Regimes for Companies Act 1967 and real estate investment trusts
On 12 September 2022, the Business Trusts (Amendment) Bill (“Bill“) was tabled in Parliament for First Reading. The Bill seeks to amend the Business Trusts Act 2004 (“BTA“) which governs the registration and regulation of business trusts (“BTs“).
Certain key amendments to the BTA set out in the Bill are as under:
(A) Re-alignment with the Companies Act
- Disclosures and trust administration. This includes requiring chief executive officers to disclose interests in transactions; requiring unlisted BTs to obtain and maintain information on beneficial ownership of their units; and simplifying the process for adopting electronic transmission of notices and documents to unitholders;
- Unitholders’ rights and general meetings. This includes expanding the scope of statutory derivative actions to include arbitration (in addition to court proceedings); adding an option for a court to order a buy-out of a BT in addition to winding up the BT; lowering thresholds for the minimum share of unitholders that are required to demand a poll; and simplifying deadlines for annual general meetings and filing of annual returns;
- Auditors and financial statements. This includes replacing the requirement for a separate directors’ report with a directors’ statement in the financial statements; removing duplication of legislation relating to independence of auditors in the BTA and the Accountants Act 2004 by deleting the relevant provisions from the BTA; requiring compliance with accounting standards formulated by the Accounting Standards Council; and requiring an auditor of a listed BT to seek MAS’ consent if the auditor wishes to resign from its position; and
- Governance and right of compulsory acquisitions.This includes prohibiting the improper use of position by an officer or agent of the trustee-manager (“TM”); clarifying that individuals (and not only corporations) are entitled to exercise the right to compulsorily acquire units held by dissenting unitholders in a takeover situation; and providing new provisions to deal with joint offers.
(B) Aligning with Corresponding Provisions of REIT Regulatory Regime
Taking reference from the REIT regime, the BT(A) Bill will strengthen the governance requirements of the BT regime by reducing the percentage of voting rights required to remove a trustee-manager from not less than three fourths to a simple majority of the voting rights of all the unitholders. This will instil greater market discipline by facilitating investors in holding TMs accountable for their performance.
(C) Miscellaneous amendments
Other amendments include clarificatory amendments, amendments to align with Securities and Futures Act 2001 provisions, miscellaneous amendments consequential to the CAAs, and amendments to reduce administrative requirements, for example, providing for:
- Passing resolutions by written means.
- Delegation of MAS Managing Director’s powers to approve exemptions under the BTA to the relevant MAS group or department head.
- Deregistration of a BT upon MAS’ receipt of the notification of completion of winding up from the TM without the need for a separate application for voluntary deregistration; and
- A trust that has received approval-in-principle to be listed on an approved exchange to be considered a BT for the purposes of the BTA, even if each of the unitholders is a related corporation of the trustee.
https://www.mas.gov.sg/news/speeches/2022/explanatory-brief-for-business-trusts-bill-2022
IRAS- Due Dates
- Estimated Chargeable Income (ECI) (September year-end): 31 December 2022
- GST Return for the Quarter July 2022 – Sep 2022 : 31 October 2022
- Form C-S/C for the FY ending 31 Dec 2021: 30 November 2022